Cybersecurity assessment of industrial automation and control systems (IACS) can be carried out using a variety of methodologies and approaches. While each approach has its merits, the IEC 62443 series of standards stands out for its ease of integration with operational technologies (OT), making it an advantageous choice.
Why 62443?
Many cybersecurity standards are successful in corporate information technology (IT) environments. However, they are not best suited to operational technology (OT) environments. The IEC 62443 series of standards, on the other hand, has been specially designed to address the security issues specific to these systems. It is the only internationally recognized consensus standard for industrial automation and control systems.
The following table compares the various recognized standards.
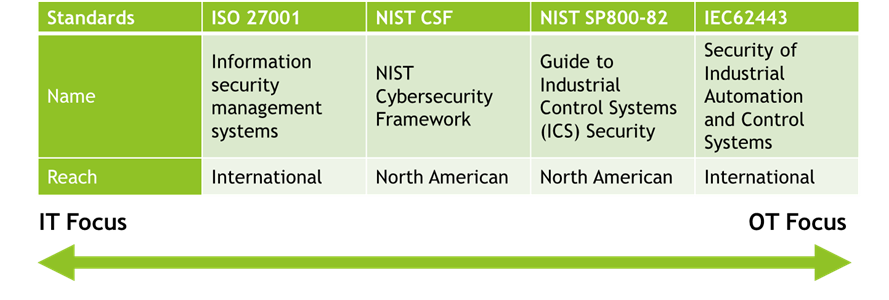
OT-focused standards are based on premises that differ from those of other standards. In an IT environment, data confidentiality is certainly the priority, while the unavailability of systems or equipment can be tolerated to a certain extent. Think of the banking sector, where a data breach represents a catastrophic scenario, whereas a service failure represents a lesser nuisance.
Operating safety, on the other hand, is simply not considered.
Conversely, on the OT side, operating safety and the availability of systems s- are the two top priorities, while data confidentiality takes second place. Think of a power plant, where the physical safety of employees and the availability of service must be preserved at all costs, while a breach in data confidentiality represents a lesser impact.
A series of standards covering several themes
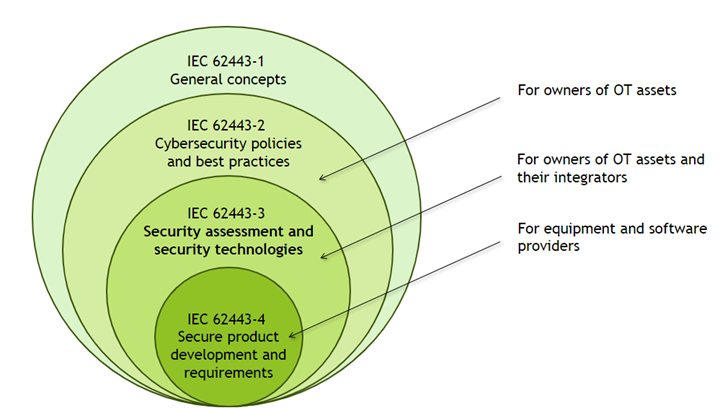
IEC 62443 is a series of standards divided into four sections (62443-1 to 62443-4), from the most general to the most specific. This division facilitates addressing the various aspects of cybersecurity in technical operations (OT).
Assessing security with standard 63443-3-2
This portion of the standard enables OT asset owners to assess the IT security of their existing infrastructure and establish target security levels for its components. Due to the complexity of OT systems, the standard proposes a methodical approach.
Standard 62443-3-2 recognizes the presence, within a single network, of components requiring different levels of protection. Typically, industrial infrastructure assets already follow the Purdue model, developed in the 1990s, which segments the infrastructure into four zones according to the types of equipment involved. While this model is a good starting point, it lacks the granularity and flexibility needed to guarantee adequate IT security.
The standard thus proposes a segmentation of the infrastructure into zones and conduits. Similar pieces of equipment that will be similarly impacted in the event of an attack are grouped into zones. The standard provides guidelines for precisely defining the different zones (for example, wireless devices should be grouped in their own zone, as should temporary or transient devices, etc.). Conduits, meanwhile, represent the communication flows between these zones. Once again, the standard provides guidelines for correctly defining conduits (for example, a conduit may not cross more than one zone).
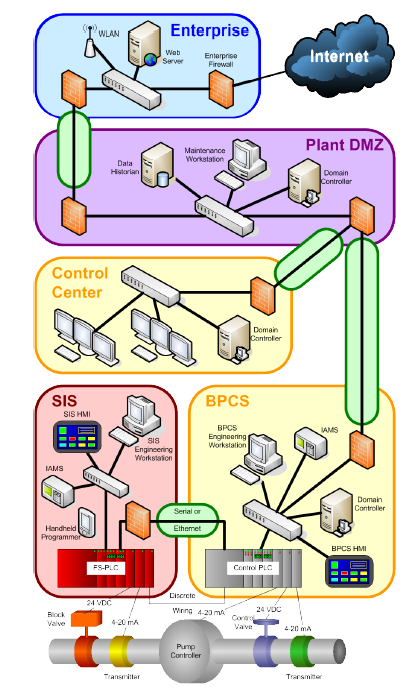
This modelling method ensures an accurate representation of the architecture and lays the foundations for future steps.
For each zone and conduit identified, the standard requires an assessment of cyber attack likelihood and impact. Using a “Probability-Impact” matrix, it is possible to qualitatively determine a cyber attack’s level of risk for each zone and conduit.
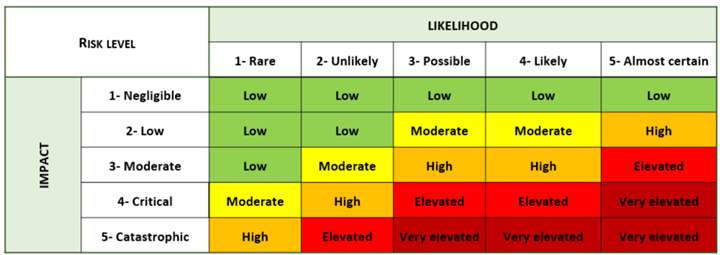
If the risk exceeds the tolerable threshold for the organization (for example risks qualified as HIGH, ELEVATED and VERY ELEVATED), this is an indication that additional mitigation measures need to be considered to reduce the impact of a potential cyber attack, or the likelihood of it occurring.
This risk assessment stage also serves to establish and record the target security level for each zone and conduit. The standard refers to this level as Security Level-Target (SL-T), ranging from SL-0 (no security required) to SL-4 (maximum security required). This target security level makes it easy to communicate to integrators and suppliers the specific cybersecurity measures to be implemented when modifying or adding equipment within the zones and conduits concerned. A matrix of the specific measures required according to the SL-T is proposed in section 62443-3-3. For example, in SL-1 zone systems, the use of shared user accounts may be accepted, whereas these are not tolerated in SL-2 or higher zones.
Numerous advantages for OT asset owners
In short, cybersecurity audits carried out in accordance with the 62443-3-2 standard offer multiple advantages for OT asset owners:
- They are an excellent first step in taking charge of cybersecurity risks, and help prioritize cybersecurity efforts, while considering the most likely risks, available resources and each organization’s risk tolerance.
- They provide a precise profile of their infrastructure assets’ IT security, based on a well-recognized standard in the industry.
- They establish the target security level (SL-T) for each zone and conduit, defining the cybersecurity requirements to be met in each case.
- They highlight zones and conduits with gaps or insufficient security.
- They enable remediation actions to be prioritized for each zone and conduit according to the level of risk associated with cyber-attacks.
Do you need help taking control of your cybersecurity? Put your trust in CIMA+ and benefit from our expertise and support in carrying out a cybersecurity audit according to standards recognized by your industry.